🌐 Introduction — Cybersecurity is No Longer a Battle of Tools, But Speed
The cyberwar dynamic has changed drastically in the last five years.
Breaches today are not happening because organizations don’t have security tools — they happen because attackers move faster than security teams can detect and respond.
AI is flipping that power structure.
Modern enterprises generate terabytes of security logs daily < SIEM dashboards flash alerts every second < SOC analysts juggle 50+ incidents a day. Meanwhile, attackers automate, launch polymorphic malware, and use AI to bypass rule-based systems.
Traditional cybersecurity is reactive.
AI makes it proactive, predictive, and adaptive.
Cybersecurity defense isn’t about building taller walls anymore — it’s about building intelligent walls that learn and fight back.
🚀 Why AI is Becoming the Core of Enterprise Cybersecurity
1. Threat volume is exploding
Cyber-attacks have grown 300% post-2020, and ransomware damages are projected to hit $265B annually by 2031 (Cybersecurity Ventures).
Human-only security teams simply can’t scale.
2. Attacks are more sophisticated
AI-powered malware learns, morphs, and hides.
Deepfake phishing impersonates CEOs.
Credential stuffing bots attack at human-impossible speed.
AI is required to fight AI.
3. Detection speed determines damage
Average breach discovery time globally is 204 days (IBM Security Report).
AI-powered systems reduce it to minutes or seconds with anomaly detection models.
Response time = survival time
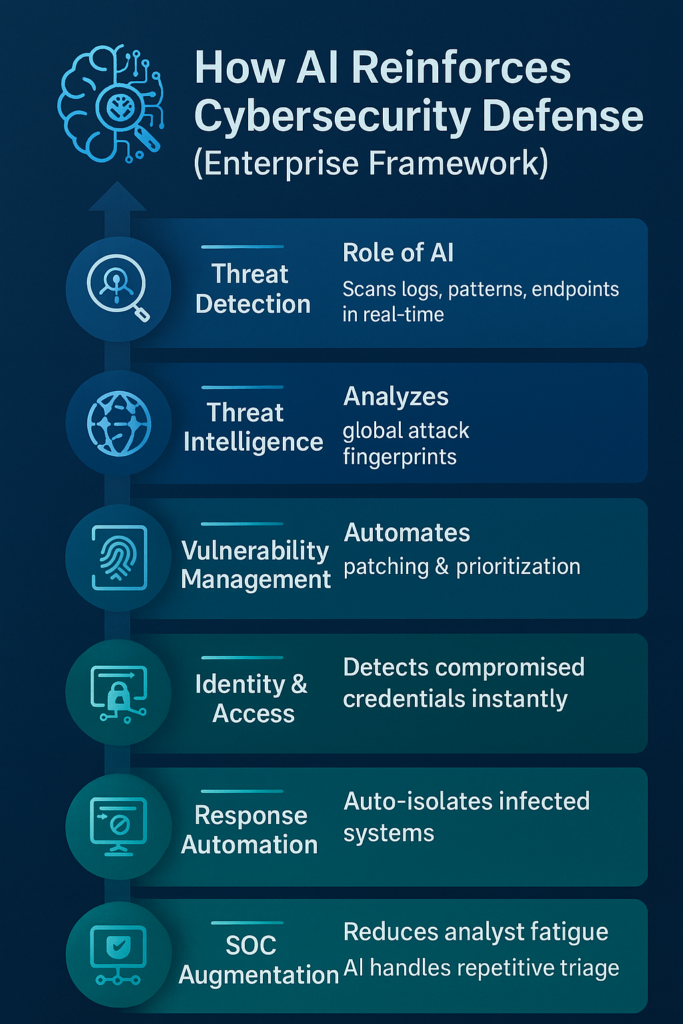
🔥 Real-World Use Cases Showing AI in Action
1. AI-Powered Intrusion Detection
Instead of rule-based alerts, AI creates behavior baselines:
- Normal login time vs unusual pattern
- Typical data flow vs sudden spike
- Usual internal traffic vs lateral movement
One unusual deviation = instant alert.
2. Predicting Attacks Before They Happen
Using global intelligence feeds, AI correlates attack signatures across regions.
Ex:
If a ransomware variant emerges in Europe → AI flags vulnerable systems in India before it hits.
3. Automated Incident Response
If malware is detected:
➡ AI quarantines endpoint
➡ Cuts network access
➡ Blocks IP/domain
➡ Generates triage summary for SOC team
Attack contained before escalation.
4. AI-Powered Email Security
Phishing detection based on:
✓ Tone analysis
✓ Link behavior patterns
✓ Sender authenticity mapping
Modern AI tools block phishing with 99% accuracy vs ~70% with legacy filters.
5. Identity Threat Detection with Behavioral Biometrics
Password alone is dead.
AI detects:
- Typing rhythm changes
- Device fingerprint variation
- Login geolocation anomalies
If login style differs — flag or block automatically.
🛡 Enterprise Cybersecurity: Old Model vs AI Model
| Traditional Security | AI-Driven Security |
|---|---|
| Reactive (after attack) | Predictive & proactive |
| Signature-based | Behavior & anomaly-based |
| Manual triage | Autonomous triage & response |
| Slow patch cycles | Automated patch orchestration |
| High analyst burnout | AI handles 70% repetitive workload |
AI doesn’t replace security teams — it upgrades them.
📌 Case Snapshot Examples
Case 1: BFSI Sector
A financial enterprise experienced 45000 daily login attempts.
AI flagged abnormal login heatmaps → detected credential stuffing → blocked within seconds.
Case 2: Manufacturing OEM
AI detected unauthorized PLC communication → isolated network segment → prevented plant disruption.
Case 3: SaaS Company
AI vulnerability scanner identified misconfigurations → ran auto remediation → compliance maintained.
Faster, scalable, self-learning security.
🔒 Where AI Makes the Strongest Cyber Impact
✔ Endpoint Detection & Response (EDR)
Stops lateral movement early.
✔ SOC Automation
AI handles Tier-1 alerts → analysts focus on strategy.
✔ Cloud Security Monitoring
Detects misconfigurations in multi-cloud infra.
✔ Insider Threat Detection
AI recognizes behavioral deviations — even from employees.
⚠ Challenges Enterprises Must Consider
AI is powerful — but not plug-and-play.
- Needs quality security data to train
- False positives must be fine-tuned
- Human oversight remains critical
- Attackers use AI too → arms race continues
Cybersecurity is a continuous adaptation battle.
💡 How Enterprises Can Start Implementing AI Security
Step-by-Step Adoption Roadmap
- Start with EDR/Next-Gen SIEM Integration
Centralize logs → feed AI models. - Adopt AI Email/Phishing Defense
Low effort. Quick ROI. - Build AI-assisted SOC
Alerts classification → automated triage flow. - Automate Patch & Vulnerability Management
Critical for ransomware defense. - Deploy Adaptive MFA & Identity AI
Passwords alone are obsolete. - Run Red Team Simulations with AI
Continuously test defenses.
FAQs
Q1. Can AI fully replace cybersecurity analysts?
No — it augments them. Humans handle judgment, AI handles analysis.
Q2. Is AI-based defense expensive?
Cloud SOC + AI tools reduce long-term breach losses drastically.
Q3. What type of data does AI need?
Network logs, SIEM data, endpoint behavior, IAM evaluations.
Conclusion — AI Isn’t the Future of Cyber Defense. It Is the Present.
Breaches are inevitable. Damage is optional.
Enterprises who combine AI-driven detection, predictive intelligence, and automated response are building cyber defense that thinks, learns, and evolves faster than attackers.
The winners of the next decade will be those who:
✔ Integrate AI into cyber strategy
✔ Build autonomous, scalable defense layers
✔ Treat cybersecurity as a continuous intelligence system
AI is not just upgrading cybersecurity — it’s reinventing it.



